Another issue you ca scratch off the list
- After providing a simple workaround, Microsoft apparently fixed this annoying issue.
- An update to Kernel-mode Hardware-enforced Stack Protection security was released.
- See for yourself how the Redmond tech company decided to tackle this security problem.

Microsoft is always releasing little updates to deal with certain flaws or problems it previously overlooked, so nothing new there.
By the way, the April Patch Tuesday updates have rolled out a week ago, so you might want to check that out as well.
Now, the tech giant may have quietly fixed a widespread issue that was affecting Windows Defender recently.
Here’s how Microsoft tackled this annoying bug
After a surge in user reports and complaints, the company confirmed that a recent Defender update, led to an error that caused the Windows Security app to wrongly display Local Security Authority (or LSA) protection as disabled.
KB5007651 (version 1.0.2302.21002), released via the March Patch Tuesday, left users worried as the message would suggest that their devices could be vulnerable.
As a result, users were failing to toggle LSA protection to on as a device restart, which was prompted by this change.
Know that it would do nothing and revert the change automatically. Basically, LSA protection would remain disabled even after the PC was restarted as instructed by the Defender app.
The Redmond-based tech giant had provided a workaround for the issue, and it basically involved dismissing such warnings.
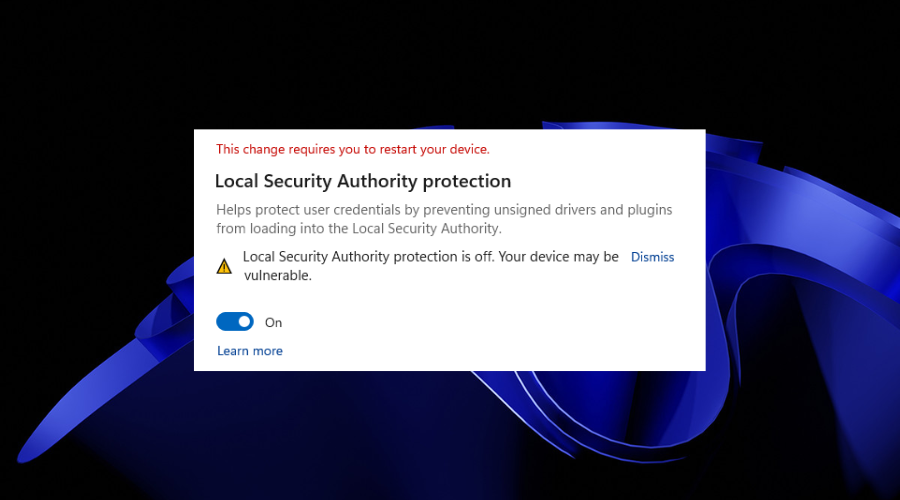
That being said, the company may have since fixed the problem with a more recent Defender update (KB5007651).
With a new update, Windows Security Service version 1.0.2303.27001 has supposedly fixed the issue, so you don’t have to worry about it anymore.
Experts suggest the issue was resolved by an update to Kernel-mode Hardware-enforced Stack Protection security feature present under Core Isolation (VBS).
This feature was introduced with Windows 11 22H2. However, KB5007651 was released nearly two weeks ago and Microsoft’s known issues dashboard still lists the bug as open.
Others are also noticing that the setting may be disabled by default, or it could be a bug. In order to use the Kernel-mode Hardware-enforced Stack Protection feature, Intel’s Control-flow Enforcement Technology (CET) or AMD Shadow Stack technology is required.
Supported chips include Intel 11th Gen Tiger Lake or newer parts, or AMD Zen 3 and newer, so please keep that in mind.
We will contatnly monitor the situation and report anything new. Share your thoughts and ideas with us in the comments section below.
Start a conversation


Leave a Comment