Readers help support Windows Report. When you make a purchase using links on our site, we may earn an affiliate commission.
Read the affiliate disclosure page to find out how can you help Windows Report effortlessly and without spending any money. Read more
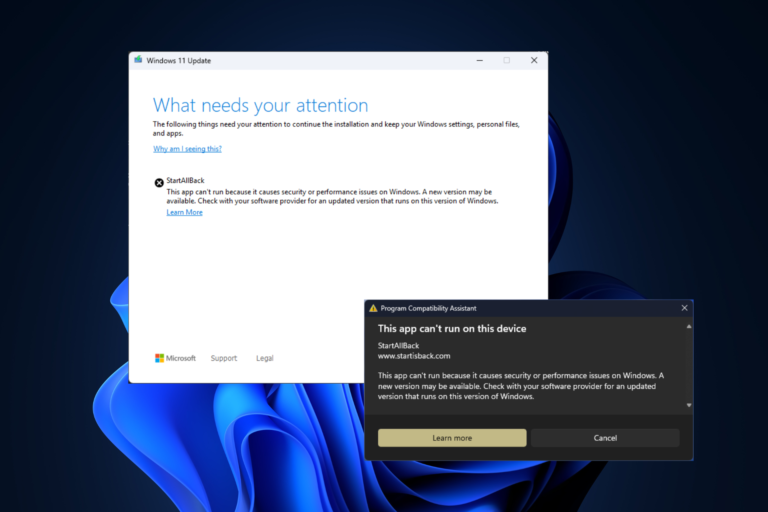
Cyber security specialists from Proofpoint and Team Cymru discovered a new malware named Latrodectus. They categorized the virus as a downloader. Its functionalities allow it to bypass detection within security sandboxes. In addition, it is similar to the IcedID family malware, and its creators might be the same. After all, the unique patterns in campaign IDs used by the Latrodectus malware resemble the ones used in previous IcedID attacks.
Proofpoint specialists found the Latrodectus malware for the first time in malicious email campaigns in November 2023. However, its usage lowered between December 2023 and January 2024. Yet, it resurfaced during February and March 2024. Additionally, there is a possibility that multiple groups of threat actors use the virus.
How do hackers use the Latrodectus malware?
According to Proofpoint researchers, the hacker group TA577 was the first to use the Latrodectus malware in one of its campaigns. Their method was to use a variety of emails with different subjects and URLs in thebody.
Afterward, the URLs would lead us to a JavaScript file. However, when opened, it runs several BAT files that use a command-line tool called curl. This method allows the malicious files to execute a specific DLL of the Latrodectus Malware. Their second attack used zipped JavaScript and zipped ISO files with an LNK file to execute the embedded DLL.
Another group of threat actors, TA578, executed a different tactic. They used contact forms on target websites and sent threatening emails with fake copyright infringement notices to which they attached carefully crafted URLs. Additionally, they used the link to send users to a Google Firebase URL containing the infected JavaScript file. After executing it, the file would install the Latrodectus malware.
How does the virus work?
The Latrodectus Malware bypasses detection using hashes to resolve the Windows OS functions. After all, this makes it harder for antiviruses to detect it. Afterward, it checks for the presence of debuggers and tries to avoid their detection.
Once the virus is in your system, it gathers information about your OS and running processes. Then, it creates a scheduled task to run periodically and an auto-run key that allows it to start with the system. Additionally, it can send your data to its command and control server, request the installation of other malware, and receive additional commands from wrongdoers.
Ultimately, more threat actors, especially those familiar with IcedID, could soon use the Latrodectus malware. The virus can send information about your system and install others. To avoid it, do not open any suspicious URLs in your email. Contact your superiors or cyber security specialists. Flag the emails and report them. Also, run an antivirus scan every week.
What are your thoughts? Did you ever receive such emails? Let us know in the comments.


Leave a Comment