We can be safer and more secure with this feature
- Microsoft has long touted the number matching feature for Authenticator.
- Starting today, number matching is actually available for MFA in the app.
- Used accordingly, it can keep you safer in this ever-changing online world.
Most of us are all about staying secure while online and protecting our identity and valuables. We should all be so concerned when it comes to online exposure.
If your next question would have been Protection from whom?, then maybe you should check out the redesigned list of threats from Microsoft.
Also, before we get into the topic, remember that Windows 11 kernel will soon boot with Rust inside. Just in case you didn’t already know.
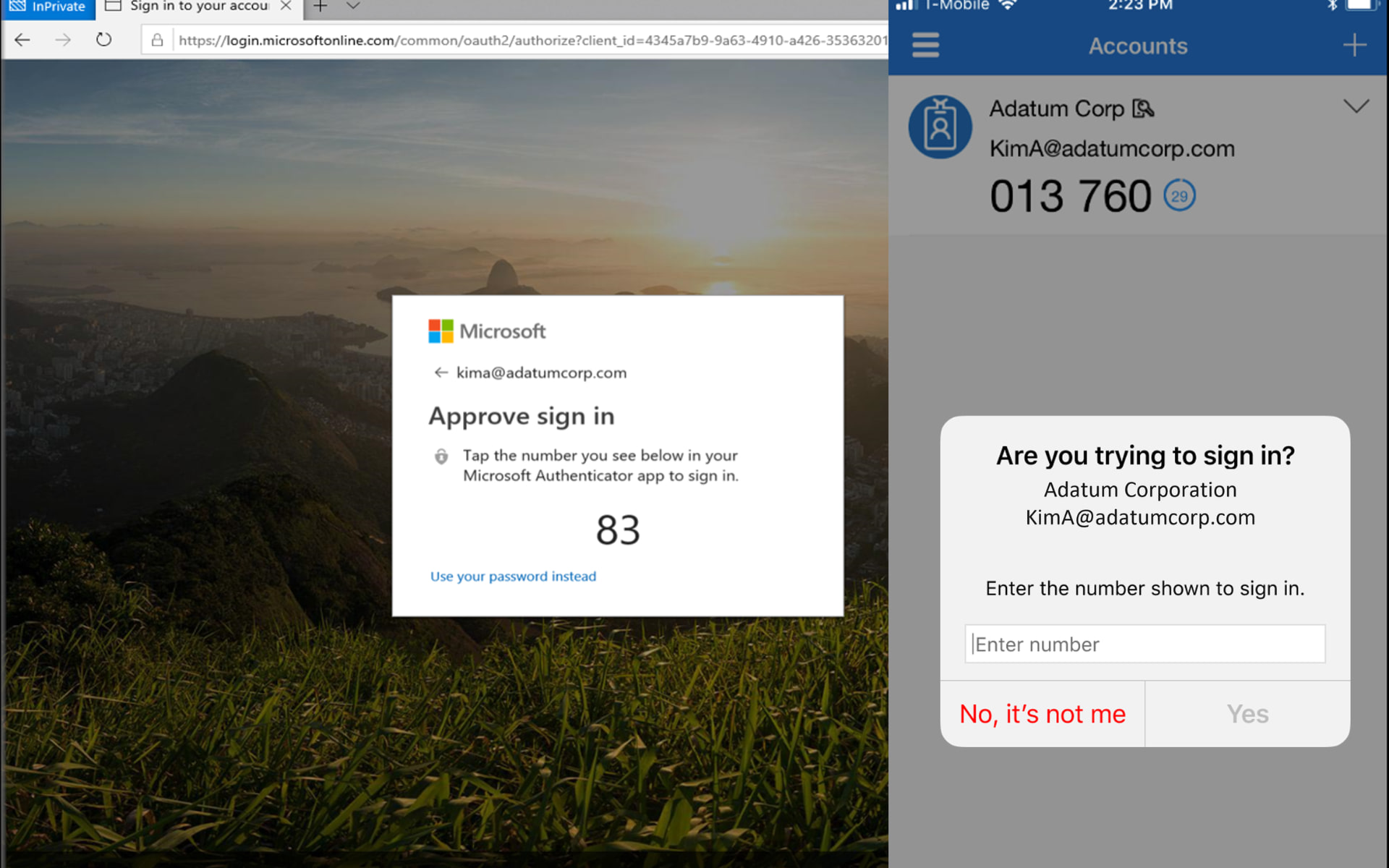
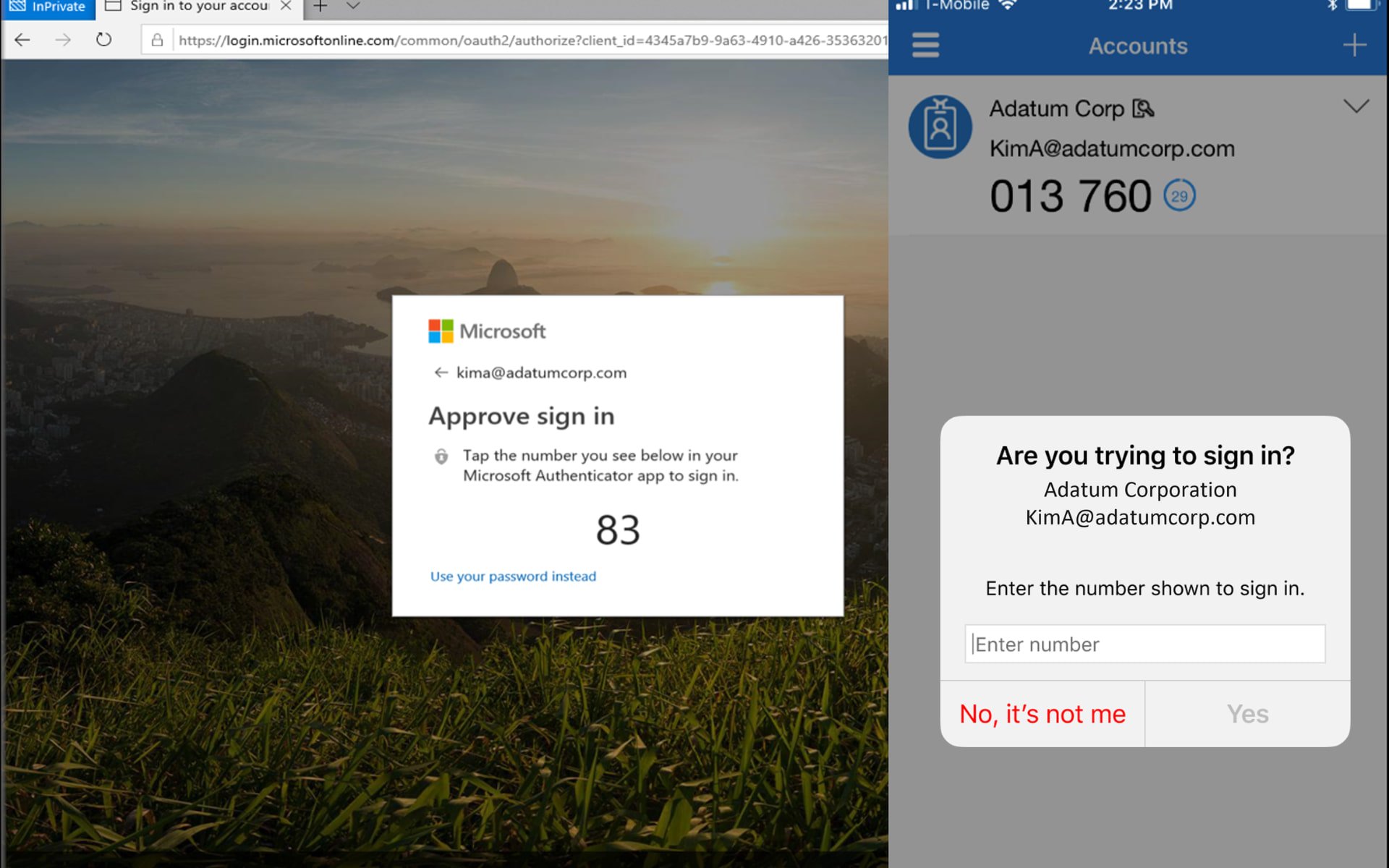
Here’s how you can stay more secure with number matching
It’s widely known that even with MFA you should be ultra-careful, as it has shown in the past that it is exploitable.
As a matter of fact, in August of 2022, Microsoft email users were falling to a new phishing attack, even with the feature on.
Fast forward a couple of weeks later, there were reports of hackers bypassing MFA and brute forcing passwords.
Not to mention that there’s also MFA fatigue or MFA spamming or push bombing attacks, which bombards the user with MFA push notifications in hopes that a user accepts the request and gives access to a threat actor by mistake.
On that note, Microsoft has decided that an extra layer of protection was necessary to fight these attempts and further secure them.
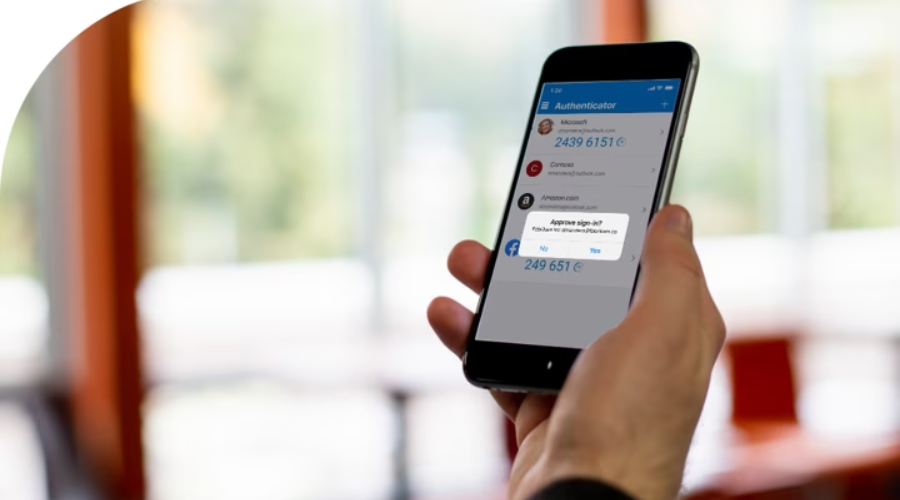
And, in order to efficiently combat such attacks, Microsoft introduced number matching as an additional step in its Microsoft Authenticator app to enhance the security provided by Multi-Factor Authentication (MFA) last year.
Starting today, May 8, 2023, the Redmond giant is enforcing number matching for all users, so that’s definitely something to be happy about.
Thus, users will need to enter the number provided into their Authenticator app when signing in, as we are about to show you below.
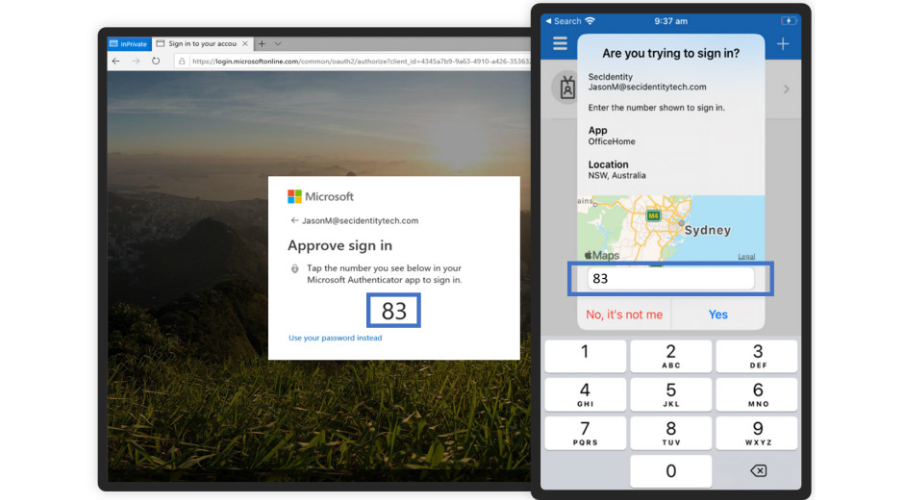
As Redmond said, number matching is a key security upgrade to traditional second-factor notifications in Microsoft Authenticator.
The company mentioned it will remove the admin controls and enforce the number match experience tenant-wide for all users of Microsoft Authenticator push notifications starting today.
Both we and Microsoft highly recommend enabling number matching in the near term for improved sign-in security.
As you know, relevant services will begin deploying these changes after May 8, and users will start to see a number match in approval requests.
Furthermore, as services deploy, some may see number match while others don’t. To ensure consistent behavior for all users, we also recommend you enable number match for Microsoft Authenticator push notifications in advance.
We’ve recently shared the fact that Windows 11 Build 25357 will absolutely bombard us with notifications left and right.
And, on the same note, we are soon going to inevitably see a lot more Microsoft-inspired ads in the Windows 11 Settings app.
What is your take on this situation? Be sure to leave your thoughts, ideas, and opinions in the comments section below.
Start a conversation

Leave a Comment